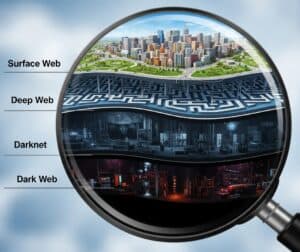
غالبًا ما تُستخدم مصطلحات "الويب المظلم" و"الشبكة المظلمة" و"الشبكة المظلمة" و"الشبكة العميقة" بالتبادل، لكنها تصف طبقات ومكونات مختلفة من الإنترنت: في حين أن الشبكة العميقة تشمل جميع محتويات الويب غير المفهرسة من قبل محركات البحث، بما في ذلك الأشياء الحميدة مثل الخدمات المصرفية عبر الإنترنت والمواقع المحمية بجدران مدفوعة، فإن الشبكة العميقة هي كل المحتوى غير المفهرس. الشبكة المظلمة هي البنية التحتية التقنية (شبكة متراكبة مثل Tor أو I2P) التي توفر إخفاء الهوية. الشبكة المظلمة هي المحتوى الموجود على هذه الشبكات المظلمة. شبكة الويب العالمية (الويب السطحي) هو المحتوى المفهرس بشكل عام.
الشبكة العميقة

The deep web represents the largest part of the internet, encompassing all content that is not indexed by standard search engines like Google or Bing. This includes a vast amount of benign and routine information that is protected or located behind a query. Access to deep web content does not require special برمجة, only direct knowledge of the URL or, more commonly, authentication. This part of the internet is a daily tool for most users.
ومن الأمثلة على محتوى الويب العميق بوابات الخدمات المصرفية عبر الإنترنت، وصناديق البريد الإلكتروني الواردة، وملفات تعريف وسائل التواصل الاجتماعي الخاصة، والمجلات الأكاديمية القائمة على الاشتراك، ومحركات أقراص التخزين السحابية، وشبكات الإنترانت الخاصة بالشركات.
السمة المميزة ليست السرية بل عدم إمكانية الوصول إلى برامج زحف الويب.
A page may be unindexed because it is behind a paywall, requires a password, is dynamically generated in response to a database query, or its owner has explicitly used a “noindex” tag. The content itself is hosted on standard server infrastructure and accessed over the conventional internet protocol.
الشبكة المظلمة
الشبكة المظلمة هي نوع محدد من الشبكات المتراكبة التي توضع فوق شبكة الإنترنت الحالية وتتطلب برامج أو تكوينات متخصصة للوصول إليها.
صُممت هذه الشبكات لتوفير درجة عالية من إخفاء الهوية لمستخدميها من خلال تشفير حركة المرور وتوجيهها عبر خوادم متعددة، مما يحجب عنوان IP الخاص بالمستخدم وموقعه.
التقنية الأبرز لتمكين الوصول إلى الشبكة المظلمة هي موجه البصل (Tor)، ولكن هناك تقنيات أخرى مثل مشروع الإنترنت الخفي (I2P). هذه الشبكات هي البنية التحتية التقنية، "الطرق" المبنية لتكون خاصة ولا يمكن تعقبها.
الغرض من الشبكة المظلمة هو تسهيل التواصل والاستضافة دون الكشف عن الهوية. يمكن استخدام هذه البنية التحتية من قبل مختلف الجهات الفاعلة لأسباب مختلفة، من الصحفيين والمعارضين السياسيين في الأنظمة القمعية الذين يحتاجون إلى حماية هويتهم، إلى الأفراد الذين يرغبون ببساطة في الحفاظ على خصوصيتهم من الشركات والحكومات. في حين أن الشبكة نفسها محايدة من حيث المحتوى، إلا أن بنيتها التي تتسم بإخفاء الهوية بشكل كبير تجعلها بيئة مناسبة لاستضافة الخدمات التي تكون الخصوصية فيها ذات أهمية قصوى. راجع مقالنا المفصل عن أدوات الشبكة المظلمة للهندسة والعلوم:
الشبكة المظلمة

تشير الشبكة المظلمة إلى مجموعة المواقع والخدمات التي يتم استضافتها والوصول إليها عبر الشبكة المظلمة.
في حين أن الشبكة المظلمة هي البنية التحتية، فإن الشبكة المظلمة هي المحتوى نفسه - "الأماكن" التي يمكنك الذهاب إليها باستخدام تلك الطرق الخاصة.
لا يمكن الوصول إلى مواقع الويب هذه باستخدام متصفحات الويب القياسية وعادةً ما تنتهي عناوين URL الخاصة بها بنطاق خاص من المستوى الأعلى، مثل ".onion" للخدمات على شبكة تور. وبسبب إخفاء الهوية القوي الذي توفره الشبكة المظلمة الأساسية، أصبحت الشبكة المظلمة معروفة باستضافة الأنشطة المشروعة وغير المشروعة على حد سواء.
في حين أن شبكة الإنترنت المظلم تحتوي على استخدامات مشروعة، مثل منصات آمنة للإبلاغ عن المخالفات ومجموعات الدفاع عن الخصوصية، إلا أنها ترتبط بشكل أكبر بالأسواق السوداء. تعمل هذه الأسواق على تسهيل تجارة السلع والخدمات غير المشروعة، بما في ذلك المخدرات، والبيانات المالية المسروقة، والبرمجيات الخبيثة، والوثائق المزورة. إن عدم الكشف عن هوية الشبكة يجعل من الصعب على جهات إنفاذ القانون تحديد هوية الأفراد الذين يديرون هذه المواقع وتحديد مواقعهم. من المهم أن ندرك أن الشبكة المظلمة تشكل جزءًا صغيرًا جدًا من الشبكة العميقة الأكبر بكثير.
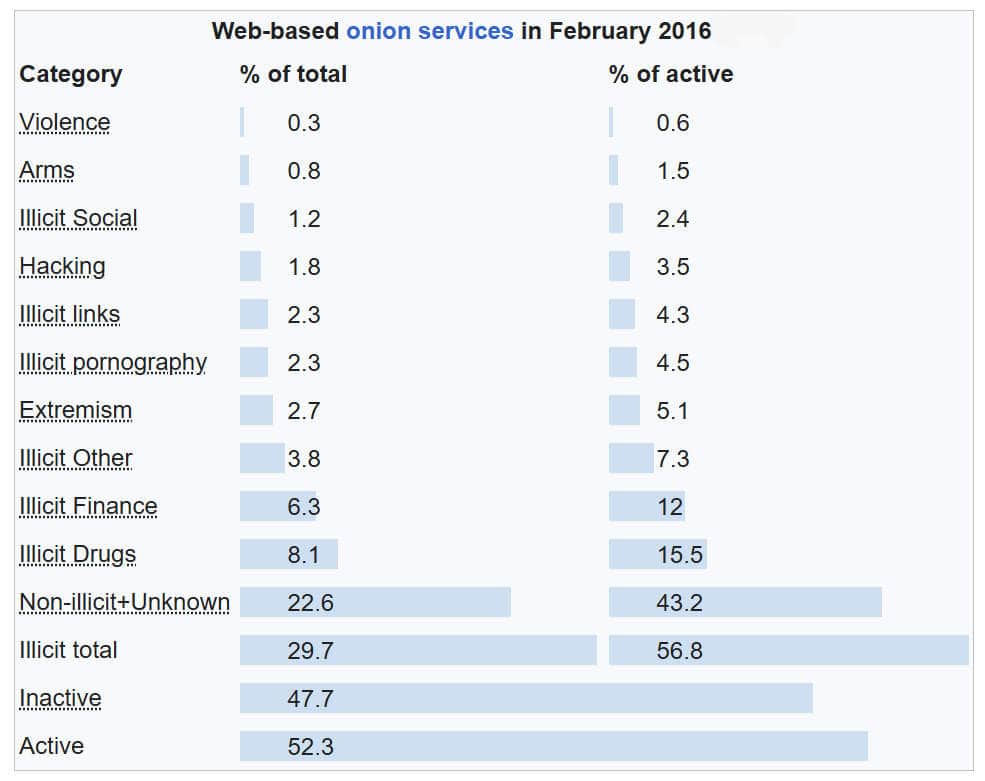
ملحوظة: يجب أن تؤخذ الأرقام أعلاه الآن للمقارنة النسبية فقط، حيث أن عدد المواقع قد ارتفع بشكل كبير منذ ذلك الحين، بما في ذلك شبكة الإنترنت السطحية (www)
المقارنة، بما في ذلك WWW
باللون البرتقالي أدناه النقاط الرئيسية لكل منها:
| المعلمة | الشبكة العنكبوتية العالمية (سطح الويب) | الشبكة العميقة | الشبكة المظلمة | الويب المظلم |
|---|---|---|---|---|
| تشبيه المفهوم الأساسي | الكتب العامة والمفهرسة في غرفة القراءة الرئيسية بالمكتبة. | مجموعة المكتبة بأكملها، بما في ذلك الأرشيفات الخاصة والأقسام المخصصة للأعضاء فقط. | نظام الأنبوب الهوائي الآمن والمجهول المستخدم لطلب الكتب من الأرشيفات وتسليمها. | الكتب والوثائق المحددة غير المفهرسة التي لا توجد إلا في أرشيفات المكتبة الأكثر أماناً. |
| التعريف | صفحات الويب المفهرسة بشكل عام والتي يمكن الوصول إليها بواسطة محركات البحث القياسية. | كل محتوى الويب غير المفهرس بواسطة محركات البحث. | البنية التحتية للشبكة المتراكبة التي توفر إخفاء الهوية (على سبيل المثال، Tor، I2P). | المواقع الإلكترونية والخدمات ("الخدمات المخفية") المستضافة على الشبكات المظلمة. |
| الحجم والمقياس | مليارات الصفحات، ولكن يُقدّر حجمها بأقل من 51 تيرابايت من إجمالي صفحات الويب. | الغالبية العظمى من الإنترنت، والتي تقدر بأكثر من 95% من كل المحتوى على الإنترنت. | بنية تحتية عالمية موزعة للشبكة. يقاس الحجم بالعقد (لدى تور آلاف المرحلات). | مجموعة فرعية صغيرة ومتقلبة من شبكة الإنترنت العميقة. تقدر بعشرات الآلاف من المواقع النشطة في أي وقت. |
| Access Method | متصفحات الويب القياسية (كروم وإيدج وفايرفوكس). لا حاجة لتهيئة خاصة. | متصفحات الويب القياسية، ولكن الوصول إليها يتطلب بيانات اعتماد تسجيل الدخول، أو عنوان URL مباشر، أو اجتياز جدار حماية مدفوع/APTCHA. | يتطلب برامج محددة (على سبيل المثال، متصفح Tor، وجهاز توجيه I2P) للاتصال بالشبكة. | الوصول إليها باستخدام برنامج معين (مثل متصفح تور) للاتصال بالشبكة المظلمة أولاً. |
| هيكلية عنوان URL | النطاقات القياسية (مثل .com، .com، .org، .gov) التي يتم حلها بواسطة نظام أسماء النطاقات العام. | النطاقات القياسية، التي غالبًا ما تحتوي على عناوين URL طويلة ومُنشأة ديناميكيًا تحتوي على سلاسل استعلام. | غير قابل للتطبيق. إنه بروتوكول شبكة، وليس وجهة ذات عنوان URL. | النطاقات الخاصة غير القياسية (على سبيل المثال، ".onion" و ".i2p") التي يتم حلها داخل الشبكة المظلمة. |
| مستوى إخفاء الهوية | منخفض. عنوان IP الخاص بالمستخدم مرئي لمواقع الويب ومزودي خدمة الإنترنت وشاشات الشبكة. | منخفض. يرتبط الوصول عادةً بهوية معروفة (اسم المستخدم، رقم الحساب). | عالية. مصممة لإخفاء عنوان IP الخاص بالمستخدم عن الخدمة الوجهة عبر طبقات متعددة التشفير والمرحلات. | عالية لكل من المستخدمين والمضيفين. عدم الكشف عن الهوية هو السمة الافتراضية والأساسية للبيئة. |
| القصد الأساسي | نشر المعلومات العامة والتجارة والاتصالات. | الوصول الآمن إلى المعلومات والخدمات الخاصة أو المحمية. | توفير قناة اتصال مجهولة الهوية ومقاومة للرقابة. | لاستضافة الخدمات ونشر المعلومات دون الكشف عن هوية المضيف أو المستخدمين. |
| المحتوى النموذجي | الأخبار، والتجارة الإلكترونية، والمدونات، والبوابات الحكومية، ووسائل التواصل الاجتماعي, تسويق المحتوى. | البريد الوارد للبريد الإلكتروني، والتخزين السحابي، والبوابات المصرفية، والسجلات الطبية، والمجلات الأكاديمية، والشبكات الداخلية للشركات. | حركة مرور الشبكة المحايدة المحتوى (حزم البيانات المشفرة). | الأسواق السوداء، ومنتديات المعارضين السياسيين، وصناديق إسقاط المعلومات الآمنة، ومدونات الخصوصية، ومشاركة الملفات غير المشروعة. |
| مشروعية المحتوى | قانوني في الغالب، على الرغم من أنه يمكن أن يرتبط بأفعال غير قانونية أو يصفها. | قانونية ودنيوية بشكل ساحق. | تقنية الشبكة نفسها قانونية وتستخدم لأغراض مشروعة. | مختلط للغاية. يحتوي على كل من المحتوى القانوني (مثل الدفاع عن الخصوصية) وكمية كبيرة من المحتوى غير القانوني. |
| ملف تعريف المستخدم النموذجي | الجمهور العام. | الأفراد المصادق عليهم (مثل عملاء البنوك والموظفين والطلاب). | المدافعين عن الخصوصية، والصحفيين، وجهات إنفاذ القانون، والمعارضين السياسيين، والأفراد المهتمين بالأمن. | طيف واسع يشمل المجرمين والنشطاء والمبلغين والباحثين والفضوليين. |
| طريقة الاستضافة | مستضافة على خوادم ويب قابلة للعنونة العامة في مراكز البيانات. | مستضافة على خوادم ويب قياسية، ولكن خلف عناصر تحكم أمنية على مستوى التطبيق. | شبكة من العقد التي يديرها المتطوعون (المرحلات) التي تمرر حركة المرور. | يتم استضافتها كـ "خدمات مخفية" على خوادم يتم إخفاء موقعها وهويتها عن طريق الشبكة المظلمة. |
| المخاطر المصاحبة | البرمجيات الخبيثة، والتصيّد الاحتيالي، وملفات تعريف الارتباط للتتبع، وعمليات الاحتيال، وجمع البيانات من قبل الشركات. | انتهاكات بيانات مزود الخدمة، وهجمات التصيد الاحتيالي التي تستهدف بيانات اعتماد تسجيل الدخول. | إمكانية إخفاء الهوية من خلال تحليل الشبكة أو الثغرات البرمجية. خطر الاتصال بعقد الخروج الخبيثة. | المحتوى المتطرف، وعمليات الاحتيال المعقدة، والبرمجيات الخبيثة، والتفاعل مع عمليات إنفاذ القانون، والمخاطر العالية للخسارة المالية. |
روابط خارجية على قوانين الإنترنت
المعايير الدولية
(حرك الرابط لرؤية وصفنا للمحتوى)





















منشورات ذات صلة
كيفية بيع الثلج للإسكيمو (أو بالأحرى حيل التسويق)
التضليل البيئي: أفضل 15 نصيحة من رجل نبيل للخداع المتقن
كيفية التعامل مع براءة اختراع معلقة بأفضل طريقة
جميع حالات براءات الاختراع: معاهدة التعاون بشأن البراءات مقابل براءة اختراع قيد الانتظار مقابل براءة اختراع منشورة مقابل براءة اختراع ممنوحة
أفضل 10 استراتيجيات وأدوات لإبطال براءات الاختراع
تقييم دورة الحياة (LCA) في تصميم المنتج على وجه التحديد